Could cars become the next target for hackers?
With in car connectivity increasingly a desirable element in the development of the latest infotainment systems and more consumers wanting to use their devices in the car, this is set to continue. Backing this up, a recent study by the IEEE claims by 2025, either Bluetooth or WiFi technologies will be in just about every new car being built. Much like the phenomenon experienced with smartphones and other consumer devices, there is a growing expectation from consumers that in-car entertainment systems should feature internet connectivity and they should enable integration with mobile devices. Coupled with more consumer service providers such as Google growing their presence in the automotive space, it is a trend set to continue.
While it has become common for consumer devices to be supplied with built-in security software or the ability to use aftermarket alternatives, few have any expectations for car security beyond alarms and immobilisers. Much like the computers first connected to the internet, current automotive architecture does not contain security measures designed to repel remote infiltration and intrusion so what are the car makers doing to resolve this?
Drivers are now seeking seamless connectivity between mobile devices such as smartphones and tablets to the car itself. Manufacturers including Audi, which recently launched LTE connectivity in cars across its range, are satisfying consumer demand for in-car internet access, with connectivity to rival smartphones and tablets. Other infotainment systems such as BMW have USB and phone connectivity, allowing users to download apps or simply transfer music files and other data from their smartphones, MP3 players and USB sticks, on to the unit’s hard disc. For industry experts this is a significant step to allow third party data onto a vehicle infotainment system.

It is worth noting that this enhanced connectivity improves the enjoyment, experience and safety for the driver and passengers but there is a downside that few have yet considered. By allowing access to the Cloud or by enabling the possibility to load unknown software and files into a vehicle is starting to raise concerns amongst leading suppliers such as HARMAN. With an estimated 25 million vehicles on the road today equipped with HARMAN audio and infotainment solutions, the firm sells its products to most of the leading car makers including BMW, Daimler, Toyota, Ferrari and Porsche. “Hacking a car remains a fairly new field but one we are investing heavily in,” says Robert Boatright, director of Automotive Networking at HARMAN. “Researchers from the Centre for Automotive Embedded Systems Security have found that it is possible to seize control of a vehicles engine and brakes by connecting a laptop to the a car’s on-board diagnostic port and hacking the vital systems. However, to date, successful car hacks have required direct hardware access to the car’s systems and few have been implemented outside of research conditions.” HARMAN’s work and knowledge of car connectivity, notably to the Internet highlights that an infotainment system connected to the internet directly or via a networked device is potentially open to cyber-attacks and malware if not sufficiently secured. The risk suggested by HARMAN is that comprehensive in-car connectivity could lead to cyber-attacks that have the potential to range from inconvenient through to impacting safety critical systems.
Drivers have long since become accustomed to using consumer devices that come ready with built-in security software or have the chance to purchase aftermarket alternatives. Few expect a need for this in the car today but HARMAN believes we have been in this scenario before. “To us, it feels like the first wave on internet-enabled computers that lacked any protection,” adds Boatright. “The car makers are only now thinking about the risk yet there are cars being shipped today with the ability to download files. The process of dealing with unwanted attention is not something new for the car makers to face. Thieves have for many years targeted vehicles and keep up themselves with trends some are still successful today taking cars despite the switch to electronic rather than mechanical immobilisation. The thieves just learnt new methods to start the car without any keys.”
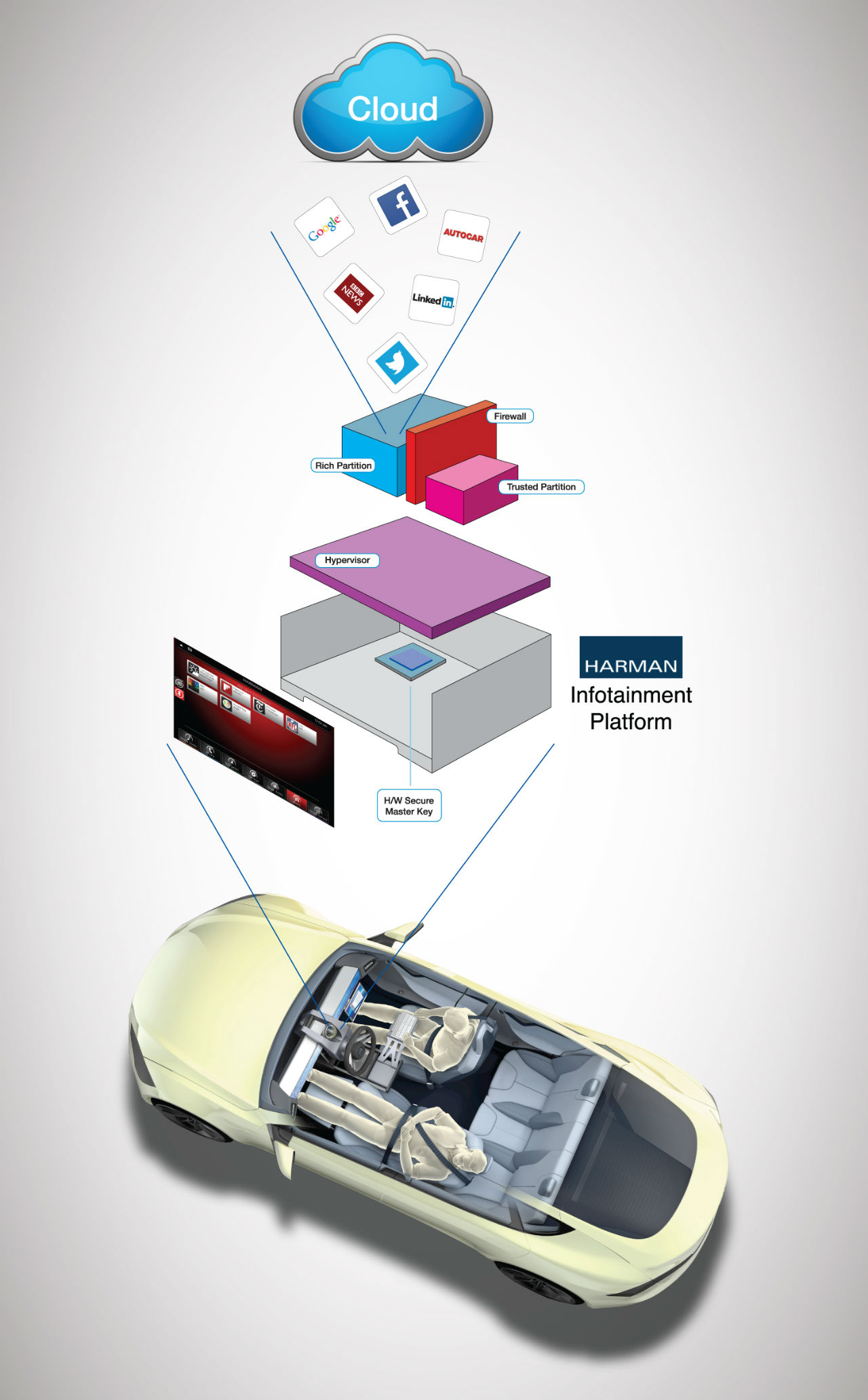 It is worth reinforcing that to date, successful car hacks have required direct hardware access to the car’s systems, such as plugging into the diagnostics port and results outside of controlled conditions suggest it is not easy. For downloads and files from the Cloud, the headunit is the first point where material could access the car and is often the connectivity gateway. Given this fact, it is also the most likely entry point for malware finding its way into the car. Malicious code could lurk behind an app downloaded or be embedded in a music file transferred onto the system via a smartphone or perhaps a USB connection. Once in the infotainment system, a virus or malware could manifest itself in a number of ways. From simply disrupting the operation of the infotainment system, such as music playback errors, incorrect navigation instructions or disrupt the display. These could be considered annoying or frustrating to an end customer but there are more serious issues. Some suggest a virus could collect personal data that is on devices connected to the network. Perhaps most concerning is the chance any virus could migrate to another in car network providing access engine and braking controls.
It is worth reinforcing that to date, successful car hacks have required direct hardware access to the car’s systems, such as plugging into the diagnostics port and results outside of controlled conditions suggest it is not easy. For downloads and files from the Cloud, the headunit is the first point where material could access the car and is often the connectivity gateway. Given this fact, it is also the most likely entry point for malware finding its way into the car. Malicious code could lurk behind an app downloaded or be embedded in a music file transferred onto the system via a smartphone or perhaps a USB connection. Once in the infotainment system, a virus or malware could manifest itself in a number of ways. From simply disrupting the operation of the infotainment system, such as music playback errors, incorrect navigation instructions or disrupt the display. These could be considered annoying or frustrating to an end customer but there are more serious issues. Some suggest a virus could collect personal data that is on devices connected to the network. Perhaps most concerning is the chance any virus could migrate to another in car network providing access engine and braking controls.
Taking inspiration from robust PC and laptop security technology, firewalls and other software security measures are being considered to act as a barrier between malware and an infotainment system. As an example, the Oakland entertainment platform presented at The Geneva Motor Show by HARMAN uses separate computing domains using type 1 hypervisor for securing critical vehicle functions from errant or malicious software for what HARMAN is claiming is “automotive grade” robustness and is the first of its kind in the industry. HARMAN’s engineers have partitioned the system into two virtual domains, one domain manages critical car functions such as vehicle network communication, and the second domain handles infotainment applications such as navigation and Internet access. The vehicle domain is securely firewalled from the infotainment domain, preventing any impact on safety-relevant features in the car. With advanced security techniques such as secure boot and data encryption such a combination creates a Trusted Infotainment Architecture that should deliver class leading security. Engineers are also looking at other measures such as developing a process that isolates crashed or compromised parts of an infotainment system from other connected components and networks.
Whilst HARMAN and others look to platforms such as Oakland, the car makers may have another alternative, particularly for those planning to offer 4G connectivity. As 4G and communications technology improves and spreads, the need to run an infotainment system on local software can be bypassed. Processing power and security duties can be carried out by a robust and remote secure server, which can then stream the required infotainment functions to a vehicle, significantly lowering the risk of malicious software from being downloaded onto an in-car system. For some, the roll out of 4G may not provide all the answers and something in the car is the favoured option for all forms of penetration.
Whilst there is a risk, HARMAN and others stress that to date no real-world occurrences of such cyber-attacks have been recorded, and for many consumers today the benefits that infotainment systems can bring to both safety and driving enhancement, certainly outweigh the potential risks to security.




